Adds intelligent network classification to network infrastructure using Network-Based Application Recognition (NBAR) principles.
Traffic can be classified in order of precedence according to groups of known ports & protocols. Provides smallest unit classification. Does not require NBAR but if available NBAR provides deep packet inspection.
Deep Packet inspection on the router.
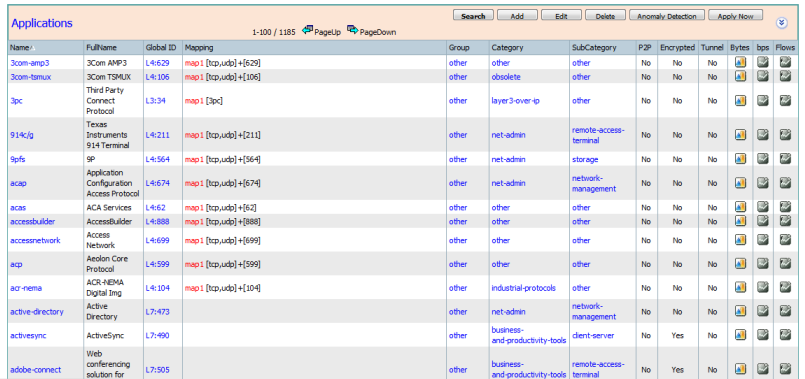
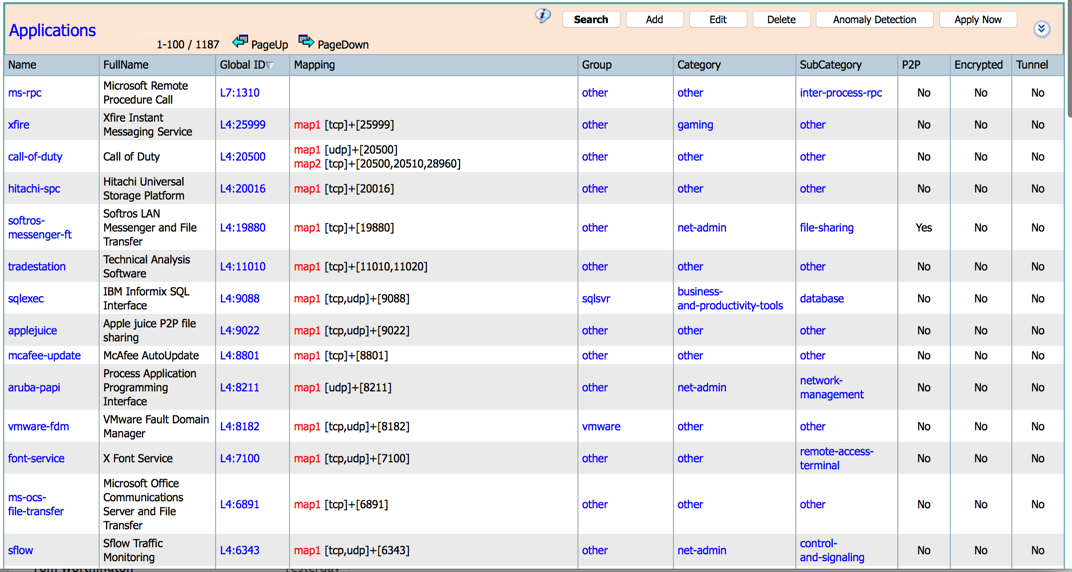
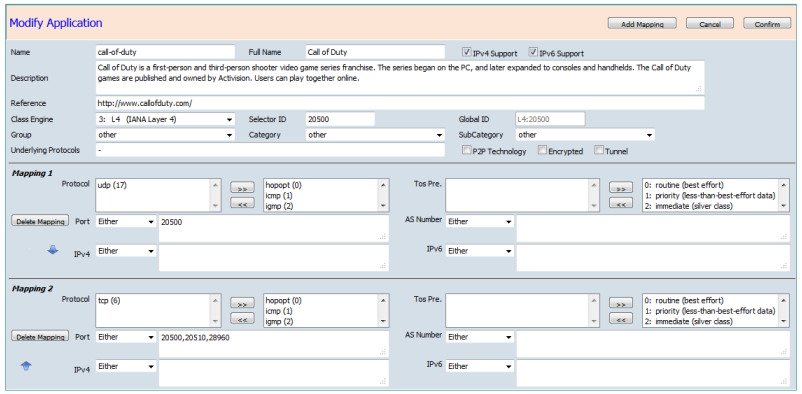
Allows traffic to be classified according to groups of protocols, port and ipv4/ipv6 addresses, ASN and ToS and categories and sub-categories of traffic and special flags such as p2p, encrypted or tunneled.
Can look into the payload and classify according to the payload content such as transaction identified, message type or similar. E.g identifying p2p traffic running on Port 80.
Simply configure NBAR to send its specialized Netflow template to CySight. Auditor will learn any new profiles and will add them to existing Application Mappings. Default Mappings are already provided for all Layers.
NBAR/NBAR2
CySight Next Generation NetFlow Analyzer fully supports NBAR2 also known as Next Generation Network-Based Application Recognition (NBAR).
NBAR2 is backward compatible and is supported on ISR-G2 and ASR1K platforms. NBAR2 is adopted as a Cisco cross platform protocol classification mechanism. It supports 1000 + applications and sub-classifications, and Cisco adds/provides new signatures and signatures updates through monthly released protocol packs.
Key Benefits of NBAR2
Advanced Classification Techniques: NBAR2 leverage classification techniques from SCE, which allow classification of IPv4, IPv6 and v6 transition techniques. NBAR2 can classify evasive applications like Bittorrent, eDonkey, Skype and Tor, as well as business applications like ms-lync, cloud applications such as office-365, and also mobile applications such as facetime, etc. using advanced classification techniques.
Field Extraction Support: It provides the mechanism to extract pre-defined fields from packet headers, which can be exported via Flexible NetFlow (FNF) for reporting.
Categorization and Attributes: It provides the mechanism to match protocols or applications based on statically assigned attributes such as application-group, category, sub-category, encrypted and tunnel. Categorizing the protocols and applications into different groups helps with reporting and applying Quality of Service (QoS) policies.
Common Protocol Library for NBAR2 Across Platforms: It offers platform independent signatures for NBAR2 supported platforms.
Signatures Delivery Through Protocol Pack: A protocol pack is a set of protocols developed and packaged together. Protocol packs are a means to distribute protocol updates outside the Cisco operating system release trains and allows more rapid, more flexible and faster adjustment to market trends. Protocol packs can be loaded on the router without replacing the IOS or reloading the device.
Custom Protocol Using HTTP URL and/or Host name: It provides the mechanism to define custom protocols to match, based on HTTP URL and/or host name.
NBAR2 Traffic categorization
NBAR2 groups applications based on various attributes such as:
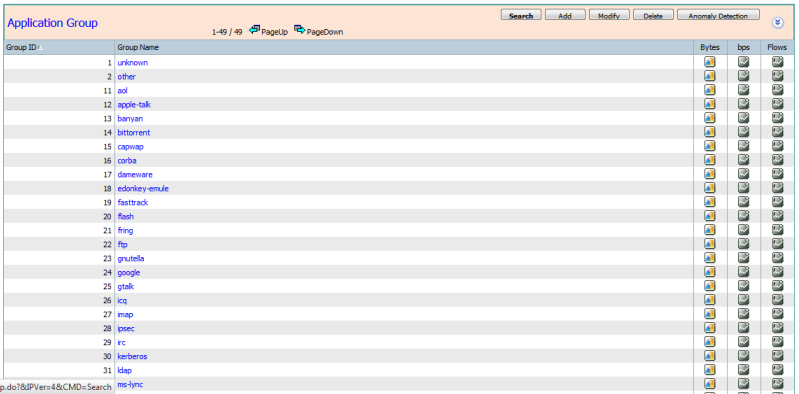
Application-group: Grouping of applications that are part of the same application suite or "brand" - e.g.: Yahoo-Messenger, Yahoo-VoIP-messenger, and Yahoo-VoIP-over-SIP are grouped together under `yahoo-messenger-group'
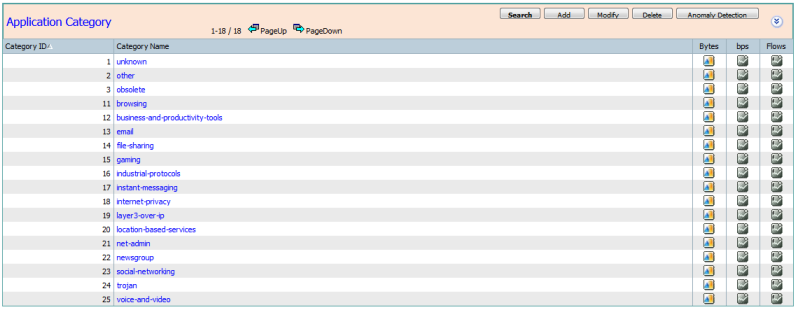
Category: Grouping of applications which support similar functionality from an end-user standpoint. E.g.: `email', `gaming', `newsgroup' etc.
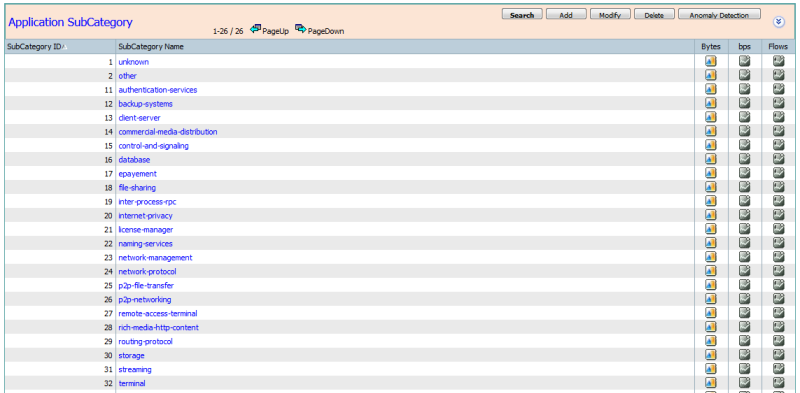
Sub-category: Similar to category, providing a secondary grouping of applications with similar functionality from an infrastructure/networking standpoint. E.g.:' routing-protocol', `database', `streaming' etc.
P2P (Peer-to-Peer)-Technology: Attribute indicates if application uses p2p technology.
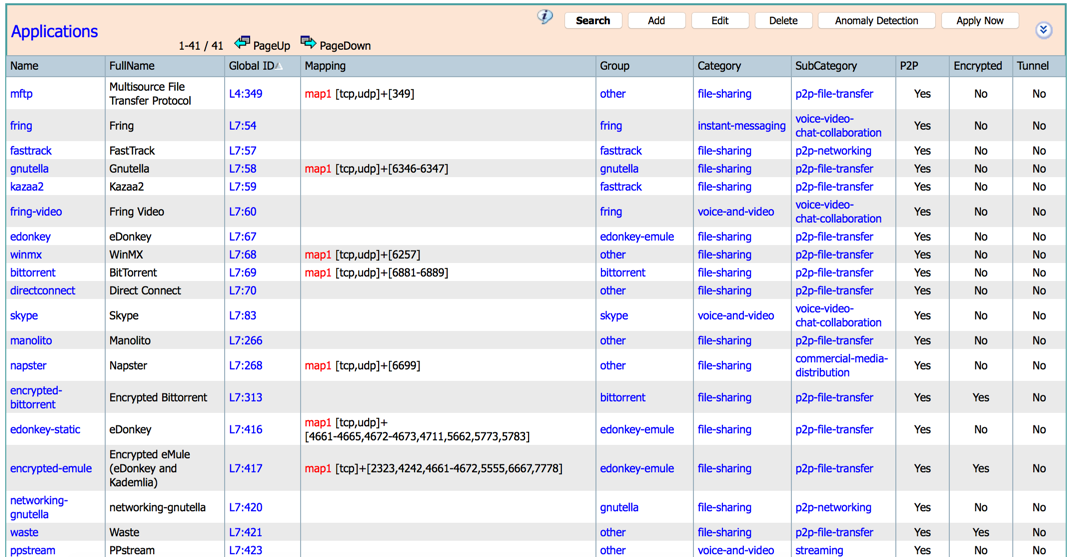 - p2p
- p2pTunnel: Attribute indicates if an application tunnels other protocols.
Encrypted: Attribute indicates if an application is encrypted.
Please visit the protocol library at this link to see how applications are categorized.
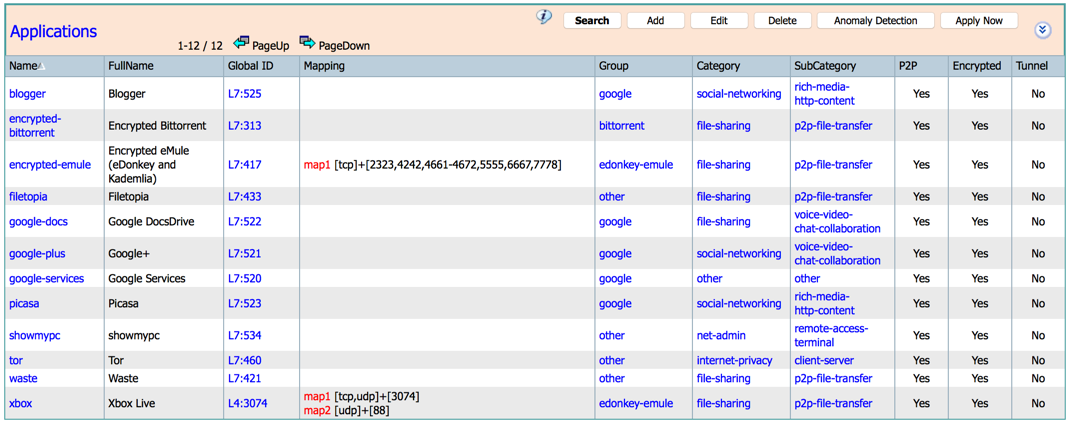 - p2p and encrypted
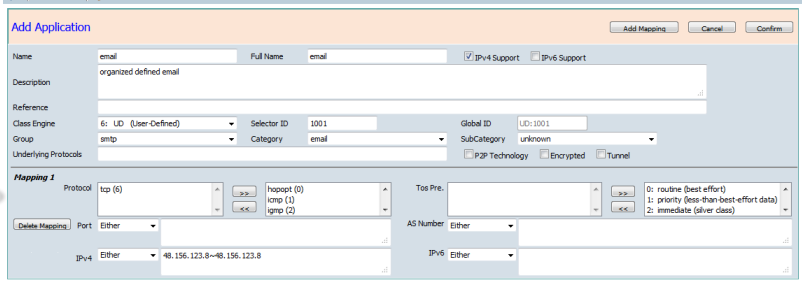
- p2p and encryptedAdd Application
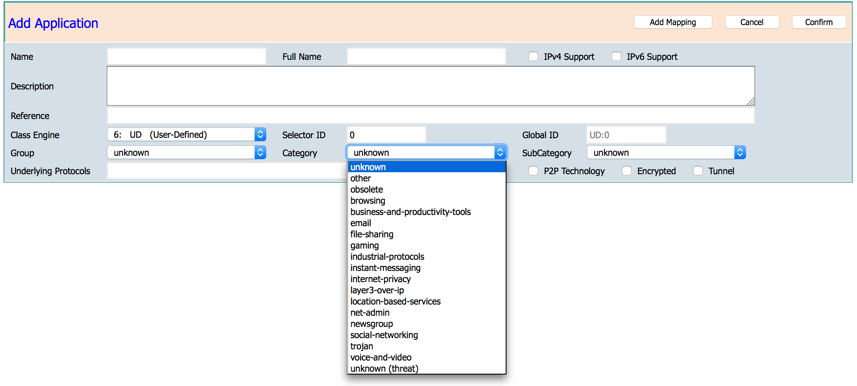
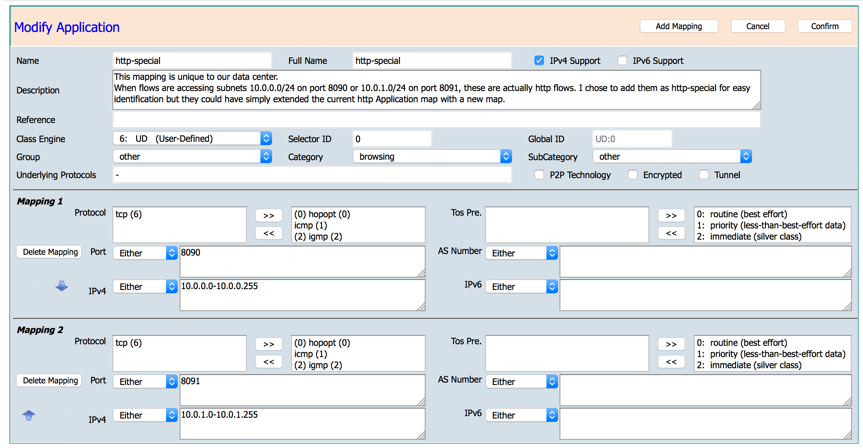
Modify Application
Application Group
Application Category
Application Sub-Category