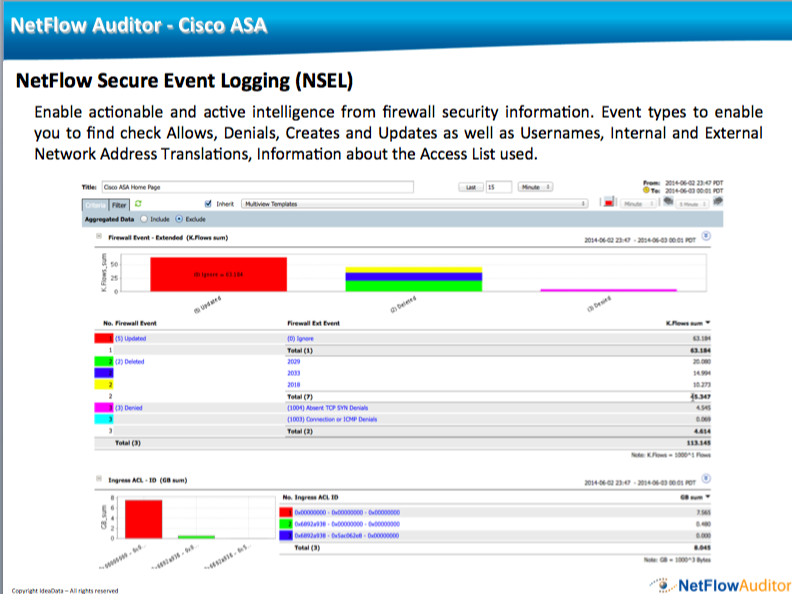
When ASA events occur on the firewall devices such as allows and denials NetFlow Secure Events will be Logged. If the NetFlow NSEL is configured these events can be sent to the CySight Collector.
PreRequisites
Please ensure you have a recent version of ASA IOS that supports NetFlow version 9 Secure Event Logging (NSEL). It is important that you use a version of the ASA operating system that correctly supports active refresh-interval (Cisco ASA v8.4(5) and v9.1(2)) otherwise you will experience false peaks.
flow-export active refresh-interval:
The flow-export active refresh-interval command is equivalent to the command “ip flow-cache timeout active”. It controls how often flows are exported to the CySight collector.
* Only exists in Cisco ASA v8.4(5) and v9.1(2)
* Not available in 8.5(1), 8.6(1), 8.7(1), 9.0(1), or 9.1(1).
For other Cisco ASA versions you have to wait for a conversation on the network to end before the flows are exported.
Therefore persistent tunnels on versions other than 8.4(5) or 9.1(2) would be problematic with reporting as the Cisco ASA NetFlow is not exported until the teardown of the tunnel.
In versions without this command the flows will generate false peaks as the flow data is only exported at once after the conversation has ended instead of exporting the flow data each minute.
ASA NetFlow export is dependent on the version of the ASA software installed. The following fields must be included in the ASA configuration to export flow data to the CySight.
CLI Configuration
The following typical commands must be included in your global service policy for NetFlow export to function. (There may be variation between version)
(config)# flow-export destination inside [CySight IP] 2055
(config)# flow-export active refresh-interval 1
(config)# flow-export template timeout-rate 1
(config)# logging flow-export-syslogs disable
(config)# access-list flow_export_acl extended permit ip any any
(config)# class-map netflow-export-class
(config-cmap)# match access-list flow_export_acl
(config)# policy-map global_policy
(config-pmap)# class netflow-export-class
(config-pmap-c)# flow-export event-type all destination [CySight IP]
(config)# service-policy flow_export_policy global
https://www.cisco.com/c/en/us/td/docs/s ... _nsel.html
https://www.cisco.com/c/en/us/td/docs/s ... _nsel.html
CySight
As long as there are no template mismatches CySight will automatically recognize the Cisco ASA flows and the Device will be present under Devices. After a minute the Cisco ASA option in the drop down menu will become available and data will be viewable using the ASA options under the Forensics Menu.
It is not recommended to send the flows via NetFlow and Syslog concurrently as this can put undue pressure of the Cisco ASA.
Configure Cisco ASA Firewall NetFlow NSEL - CySight
This area will help fast track you in planning, setting up and managing NetFlow in your environment. NetFlow is an embedded instrumentation within Cisco IOS Software to characterize network operation.
Network specialists of various levels within an organization need to be able to report on traffic traversing sites, key links and data centers without deploying probes. They use CySight powered by unique NetFlow Auditor methods of scalable collection, retention and Predictive AI Baslining to capture and analyze every NetFlow record with aggregation options and small footprint real-time and long-term storage. From Telco to SME you will recognize the superior reliability and performance of the CySight NetFlow Auditing solutions, as well as the management benefits offered.
Network specialists of various levels within an organization need to be able to report on traffic traversing sites, key links and data centers without deploying probes. They use CySight powered by unique NetFlow Auditor methods of scalable collection, retention and Predictive AI Baslining to capture and analyze every NetFlow record with aggregation options and small footprint real-time and long-term storage. From Telco to SME you will recognize the superior reliability and performance of the CySight NetFlow Auditing solutions, as well as the management benefits offered.
1 post
• Page 1 of 1
-
//
- Site Admin
- Posts: 1
- Joined: Wed Sep 22, 2021 9:22 pm
1 post
• Page 1 of 1